Cyberchiefs
= detailed study of Peer Governance in "online tribes"
Book: Cyberchiefs. Autonomy and Authority in Online Tribes. Mathieu O’Neil. Macmillan/Pluto Press, 2009.
Commentary
Michel Bauwens:
"Peer production is by now a very accepted term and concept and it has its classic study, i.e. The Wealth of Networks by Yochai Benkler. But I can’t really say that the second concept of the P2P Theory trilogy, i.e. peer governance, has taken off in any real sense, though many studies do tackle the governance of open source communities, but without naming it as peer governance. Does this mean that researchers do not recognize this as a separate area of study?
In any case, the classic study there is Steven Weber’s The Success of Open Source.
Now however, comes a second book: while I have to reserve my judgment, as I have just started reading it, I think it’s fair to say that it is the very first monography to specifically tackle the study authority and leadership in peer production communities. So I find this publication significant, as a founding moment for the dedicated study of peer governance, even though the author does not use the concept.
Introduction
Publishers' Summary
Cyberchiefs. Autonomy and Authority in Online Tribes:
“People are inventing new ways of working together on the internet. Decentralized production thrives on weblogs, wikis and free software projects. In Cyberchiefs, Mathieu O’Neil focuses on the regulation of these working relationships. He examines the transformation of leadership and expertise in online networks, and the emergence of innovative forms of participatory politics. What are the costs and benefits of alternatives to hierarchical organization? Using case studies of online projects or “tribes” such as the radical Primitivism archive, the Daily Kos political blog, the Debian free software project and Wikipedia, O’Neil shows that leaders must support maximum autonomy for participants and analyses the tensions generated by this distribution of authority.”
Author's Motivation
Mathieu O’Neil on Why I wrote ‘Cyberchiefs’:
“I wanted to answer this question: how does power operate within groups who reject domination? How do leaders justify their authority in anarchistic communities on the Internet? This meant that there needed to be a new theory of power, something which sociology was uniquely equipped to do, but which had not yet happened. This theory would have to take into account the different dimensions of power online: power as an archaic force (a male universe of hackers); as a collectivist enterprise (the rejection of traditional forms of hierarchy); as the affective recognition of the extraordinary brilliance of great individuals and the extraordinary position of great nodes on a network - but what happens to charisma when it is distributed?
I did my PhD research on zines (idiosyncratic marginal magazines) in the San Francisco Bay Area in the nineties. My approach was influenced by Pierre Bourdieu: here is an underground market with its own rules of the games, systems of oppositions, and it is a way for people to show how ‘cool’ they are in relation to mainstream culture. So in a sense they are really reproducing dominant patterns of cultural distinction. But, there are oppositions as to what constitutes ‘coolness’ between punks who reject correct discourse, and others who embrace correction, which reflect different positions in the social space, and different strategies for political enagagement.
One thing that really interested me at the time is how do you make people respect the rules of reciprocity in autonomous fields without formal justice and police systems? Apart from public shaming, there wasn’t much that could be done about people who didn’t send zines even though someone else had send them a zine or a few dollars. I was also interested in the networking aspect: who is a hub, who operates as a bridge between disconnected groups, etc.
When weblogs started I was struck by the similarity with zines: blogs were going to ‘retake the media’, and so on. So I started looking at them, doing surveys like I had done with zines. I also learnt more about webmetrics; about social network analysis and network theory mechanisms such as ‘preferential attachment’ (new entrants on networks tend to link to the incumbents: the centrally located - the rich - always get richer, the poor can never catch up). I looked at social anthropology (conflicts, boundaries, monstrous ‘others’) and political anthropology (tribes as societies against the state, as rejection of separated power), I spent a lot of time with political philosophy (the public sphere, counter-publics) but ended up cutting that chapter out, and the biggest new influence was perhaps Luc Boltanski and the key concept of justification; also his idea that it is not just sociologists who can understand and uncover domination (what Bourdieu or Foucault say) but that ordinary people have reflexivity, can evaluate the respective claims of people during conflicts.
All this inexorably led me back to a founding block of sociology, Max Weber’s classic theory of legitimate power or authority. Justification is not so different from legitimation. The starting point to forge appropriate conceptual tools for the analysis of leadership in online settings is the recognition that on the Internet authority must integrate autonomy or risk being rejected as overly authoritarian. In the online context, administrative authority is the capacity to exclude people from a network, or to limit the actions they can undertake on that network. The distribution of administrative authority to autonomous individuals is an essential part of the appeal of mass volunteer projects such as Wikipedia, because it gives new entrants the possibility of rapidly attaining positions of power.
Weber distinguished four types of social action: traditional, affectual, instrumentally rational and value-rational. (1) The first three forms correspond respectively to traditional (hereditary), charismatic (revolutionary) and legal-rational (bureaucratic) bases of authority. Weber did not equate the last form of social action to a specific authority type. Organisational scholars have argued that value-rational social action was apparent in egalitarian or collectivist forms of organisation such as, in the 1970s, free schools and clinics or alternative newspapers; (2) and, in the contemporary period, self-organised Internet communities such as the Debian Free Software project. (3) But while organisation science provides useful tools for the analysis of Internet sociality, it fails to take into account the full range of authority types which occur in online communities. In the case of Wikipedia for example, the project founder’s charismatic prestige routinely allows him to legitimately overrule collective decisions.
What is the impact of online networking on charisma? To answer, the origins of this variant of legitimate power must be considered. Computer engineers or “hackers” (not to be confused with computer vandals or thieves) created the Internet’s protocols. If computer code was efficient and elegant, its author was rewarded with high status; more recently, great figures in the Free Software galaxy, who aimed to protect code from the impurity of copyright control, have been described in quasi-mystical tones. (4) In the process scientific expertise became independent from hierarchical organisations: hackers recognised only the judgment of their peers. The authority of experts is traditionally subordinated to the authority of leaders. However when the Internet was developed learned authority to a great extent determined administrative authority, as only computer hackers knew how to run the systems. Following the lead of hackers, expertise on the Internet became dependent not on credentials issued by an institution to an individual, in the shape of a diploma or professional certificate, but on an individual’s unique skill, developed over time, and publicly demonstrated.
Beetham (5) suggests that two legitimising principles are more emancipatory than others. The first is the principle of democratic sovereignty, based on the collective will of the group. The second is the meritocratic principle of differentiation which, in theory, challenges the reproduction of advantage. On the Internet, meritocracy was separated by hackers from institutional hierarchy and bureaucracy. Merit assumed an anti-authoritarian slant, based on the regard for the charismatic genius of great initiators (hacker-charisma), and, subsequently, on the charismatic position of great nodes (index-charisma), the latter determined by the aggregation of the decisions of multiple individuals, as exemplified by Google’s PageRank algorithm.
The principles of autonomous charisma and democratic sovereignty structure online authority. It should also be noted that there is a clear gender imbalance in the distribution of prestigious founders and central nodes: early entrants in online communities, who benefit from “preferential attachment” (6) are predominantly male. This imbalance is accompanied by the persistence of archaic forms of domination based on a masculine logic of conflict and honour, apparent in such behaviour as trolling and flaming. Apart from the relationship between autonomy and authority, I wanted to understand how new forms of leadership and expertise challenge or conform to informational capitalism; how communities address sexism, hierarchy, equality, justice and bureaucracy according to the structure of their relations of authority; and what this means for the future of autonomy. ”
References
(1) Max Weber (1978 [1922]) Economy and Society. An Outline of Interpretive Sociology, Berkeley, Los Angeles and London: University of California Press.
(2) Joyce Rothschild-Whitt (1979) “The collectivist organisation: An alternative to rational-bureaucratic models”, American Sociological Review, Vol. 44, No. 4, pp. 509-525.
(3) Siobhán O’Mahony and Fabrizio Ferraro (2007) “The emergence of governance in an open source community”, Academy of Management Journal, Vol. 50, No. 5, pp. 1079-1106.
(4) Moody, Glyn (2001) Rebel Code. Linux and the Open Source Revolution, London: Allen Lane.
(5) David Beetham (1991) The Legitimation of Power, London: Routledge.
(6) Albert Barabàsi (2002) Linked: The New Science of Networks. Cambridge, MA: Perseus.
Excerpts
Typology
From Chapter 4, The Grammar of Justice (pp. 87-89):
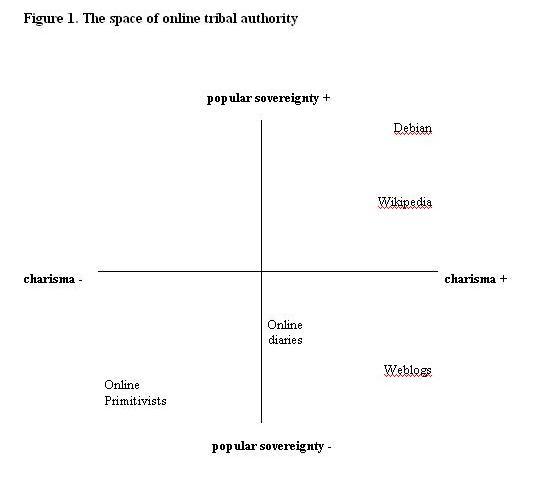
"Since the mid-to-late 1990s and the democratisation of Internet access, non-technically able users have joined in online information sharing and cooperative work. In today’s Web 2.0 environment, the range of those who exercise technical control has dramatically risen. Examples dealt with in this book include Wikipedia articles and progressive political weblogs. Figure 1 presents a spatial representation of the field of online authority in the form of four quadrants intersected by two main axes of charisma and sovereignty. Online tribes are positioned in the quadrants according to the structure of their authority relations.
The top-left quadrant is empty as it corresponds to the space of governementality: that is, popular sovereignty with no autonomy. An example would be the online networks developed by political candidates to give their supporters the impression that grassroots activism is taking place.
The schematic representation of the space suggests that online authority regimes do not exist in a perfectly pure state, but rather in various forms of combinatory amalgamations. Since sovereign and charismatic authority tend to contradict one another, can we expect to find an especially high occurrence of conflicts in the top-left quadrant, where the overlap is the strongest? And what are the consequences of rejecting all forms of authority, as in the bottom-left quadrant? An important question for understanding online authority concerns the passage from autocratic systems based on charismatic authority to democratic systems based on sovereign authority, as occurred in LambdaMOO, or in the Debian free software community. What factors enhance or prevent the emergence of more democratic forms? If the quest for justice is a driver of a change in authority regimes, why does the contestation of archaic force on weblogs not lead to the development of sovereign authority?
A central tenet of pragmatic sociology’s focus on action is that research should endeavour to determine how online authority is justified in situation. To this end, the following four chapters propose case studies of online tribes, which will serve to illustrate the different positions in the space of online tribalism as represented in figure 1. The four tribes are: radical anarcho-primitivist websites and forums (lower-left quadrant); progressive political weblogs (lower-right quadrant); the Debian free software mailing lists and the English Wikipedia wiki and mailing lists (upper-right quadrant). As mentioned above, the upper-left quadrant is tribeless. The analysis will compare the four tribes in terms of three main parameters: project and space, authority structure, conflicts and enemies. These categories are briefly presented in the remainder of this chapter.
Project and space. How does the project embody autonomy? What kind of computer-mediated communication is it, what technical possibilities are available for ordinary users? In terms of participation, how does recruitment operate, what kind of contract is offered to new entrants – what are their roles, duties and privileges? How are boundaries maintained? Finally, how do tribes deal with the embedding of online autonomy in network capitalism?
Authority Structure. What is the relationship between expertise (learned authority) and leadership (administrative authority)? To what extent is charismatic or sovereign executive authority distributed? What are the tools of governance, such as norms and rules, monitoring, adjudication, and enforcement mechanisms? Is authority strong, weak or inconsistent?
Conflicts and enemies. Since antagonism is central to tribal activity, a particular focus of analysis will be conflicts. Rules regulate the integration of patches or the positions of people. Conflicts, triggered by the application, justification or absence of rules, are the means by which people affirm their adherence to, or rejection of, the rules and the authority order which they underpin. A central concern will be the role of enemies. The definition of outside enemies is vital to coalesce project cohesion and exclusionary boundaries. This is all the more the case when projects experience internal conflict: outside enemies will help to reinforce project solidarity."
Governance in Debian
From Chapter 7, The Imperfect Committee: debian.org (pp. 133-141)
‘The Cathedral and the Bazaar’ is the title of a famous essay by Eric Raymond. Raymond contrasted the secretive low-frequency-release model of Richard Stallman’s Free Software Foundation’s GNU software to the ‘release early, release often’ model pioneered by Linus Torvalds with Linux. Nicolas Auray has argued that Debian represents an attempt to make the bazaar viable, with norms aiming to reduce tensions, but also moral, with institutions aiming to reduce unequal relations. (1) This represents an evolution for FOSS projects from purely charismatic models such as Linux which are based on a ‘lazy consensus’: if no one makes an objection after three days, then a proposal is accepted. (2)
Debian must reconcile the central notion of each developer’s autonomy, and the respect for difference, with the constraints deriving from the production of a complex system with quality standards of the highest order. This is the main purpose of the modular structure: to give developers full administrative control over their packages or teams, in a mini-cathedral model. This level of personal control is in fact a primary attraction for many FOSS developers, who are then free to work alone if they wish. There is also less chance of being criticised for one’s work if one keeps control over it and only releases finished versions, thereby stopping others from interfering. At the same time, Debian packages all follow strict production guidelines (‘policy’) and can easily become integrated.
The absence of monetary rewards in Debian guarantees that reputation benefits earned by technical excellence (hacker charisma) are the standard for all value. One sign of authority in Debian might therefore be the number of packages any one developer is responsible for: the higher the number, the greater the hacker-charismatic authority? Yet a higher level of administrative authority is required to deal with infrastructure that stretches over different packages. Martin Krafft observes that these core tasks are undertaken ‘by a smallish number of developers that take Debian very seriously’. (3) Studies of other free-software projects have shown that small groups are responsible for the majority of work. Lerner and Tirole argue that a tiny minority make the largest contributions, their integration into the ‘core group’ of developers representing the ultimate recognition by their peers. (4) A study of the development of Apache showed that out of 400 developers, the top 15 contributed between 83 and 91 per cent of changes, whilst ‘bug’ (or problem) reports were much more evenly distributed. (5)
Krafft notes that since the membership of the security team is seen as prestigious, ‘some people write lengthy emails explaining why they should be picked’. (6) Naturally these requests are never honoured: only those who have contributed are deemed worthy of inclusion. Highly specialised knowledge of the project’s infrastructure or of the workings of a core team, accumulated over years, risks becoming fossilised. This is the central question for Debian, and indeed for any volunteer project requiring high levels of expertise: how do the tribal elders transmit their wisdom? As will be shown in the next section, this question is largely unresolved.
Supporting new users is a crucial activity if the project is not to wither away. Hacker-charismatic authority can be detected by examining interactions in lists, the project’s primary communication and education tool. FOSS lists are not simply forums for discussion, but are also means for peers to evaluate the quality of code or advice. A question must be useful for everyone, otherwise it risks the indignity of the questioner being directed to documentation such as the FAQ. (7) Studies of patterns of questions and responses on the debian-french user list reveals a tension between a system of massively distributed collective authority in which everyone and anyone authorises themselves to respond to a request on the one hand, and the constitution of an elite based on reciprocal approbation on the other. The selection of who one responds to, as well as how one responds, is crucial: authoritative responses on threads are primarily addressed to previous respondents, rather than to the original questioner. The threaded nature of discussions on lists enables the selection of high-status partners. A mutually responding core emerges, which preserves expert authority in the midst of a dynamic and open system. (8) On developer lists, studies show that the necessary knowledge of all the elements of the distribution, allowing people to foretell problems and remember solutions, is not equally distributed. List archives can be viewed as the minutes of a permanent assembly, which is directly accessible to all at every minute, but only the most experienced members can remember or find their way around the mounds of archived information. The authority of such tribal elders represents the means of moderating the obsessional reference to technical excellence. (9)
Unlike on Daily Kos, where the two variants of online charisma mutually reinforce one another, hacker and index charisma on Debian are fundamentally antinomic. This is because index authority always contains an arbitrary element: the identity of earliest entrants is due to chance, not talent. Since Debian is based on meritocratic skill, it should in theory have no place for the other form of online charisma. How did the index-authority virus enter the project? As previously mentioned, a key goal for leaders of online tribal projects is to distribute administrative power whilst maintaining quality. Since the autonomous structure makes it very hard to discipline people, the maximum effort must be borne upstream, before recruitment occurs. In practical terms, this boils down to: who can be trusted to access the levers of control? Contrary to weblogs (where administrative power is never fully opened to everyone) and to wikis (where all modifications are instantly reversible, and do not affect the whole project), contributors to Debian really do have the potential to harm the software.
As a result, a central difference between Debian and the other cooperative projects examined in this book is that contributions cannot be anonymous. Online communities are routinely described as having fluid boundaries and shifting members and identities. In contrast, members of FOSS projects who are developing software that is hosted on protected servers connected to the Internet must maintain a distinct and trusted identity, which will enable them to gain access to these protected resources. (10) Since developers are capable of modifying the code, the project has to be protected from Trojans (hidden bugs or viruses) as well as from well-intentioned but unskilled developers.
There are various means by which a digital identity can be authoritatively linked to the entity it claims to represent. The answer for Debian lay in the use of keys (large numbers) that allow data to be encoded and decoded. If the key is secret, and the same key is used to encode and decode a message, sender and recipient cannot exchange a secret key to begin with. A possibility is public key infrastructure, where a centralised certifying authority registers users and delivers certification to them. But autonomous projects require a distributed solution. The aim of securing identities led to the establishment of a private-key cryptography system, whereby a public key encodes data, and a completely different key decodes the data. The authenticity of the communication’s content is guaranteed, but this process does not verify the link between the key and the sender’s identity. Real-world identities must be connected to a given public key. This is achieved when identity certificates (including public keys and owner information) are signed by other users who are themselves known and trusted by the tribe. The physical act of vouching for the link between a public key and the person or entity listed in the certificate takes place at offline ‘key-signing parties’. Developers bring a copy of their public key and valid photo identification; they meet and certify another’s public key. A key which has been signed can then be placed on a central key server maintained by a keyring coordinator. In social network analysis terms, O’Mahony and Ferraro write that the resulting web of trust rests on the assumption that ‘the more people who have signed each other’s key (the greater is the density of the network), the more reliable is the information authenticated’. (11)
This process contains the hallmarks of a familiar scenario in which entrants who have accumulated many endorsements are advantaged and it is hard for new entrants to break in. O’Mahony and Ferraro have analysed the dating of key-signings and suggest that between 1997 and 2001 the Debian keyring network increasingly conformed to a power-law mode and became centralised. Formalised membership processes, such as a vetting team (the New Maintainer Committee or NMC) and the requirement of sponsorship by an existing developer, encouraged preferential attachment to gatekeepers, as measured by key-signings. O’Mahony and Ferraro’s conclusion, that becoming a central player through physical participation in key-signings ‘enhanced the probability of attaining a gatekeeper position far more than the number of packages maintained’, (12) seems unassailable. However their assertion that preferential attachment influences the ‘structure of the network as well as the design of governance mechanisms’ assimilates recruitment procedures to overall project governance. There is scant evidence that this is the case, beyond the fact that the head of the NMC was elected Debian project leader in 2003. It is arguable, for example, that membership of Debian’s Technical Committee (TC), or of key infrastructure teams, is of greater significance to the project, because these positions are not renewed every year.
The influence of index-charisma is counterbalanced by Debian’s embrace of sovereign authority. An egalitarian or collectivist organisation based on the sovereign will of all participants is the natural format of ‘successful anarchist communities’. (13) This takes a number of institutional forms. The autonomous authority of individual developers over their packages is overridden by the greater good, as expressed in two institutional mechanisms: the General Resolution Protocol and the Technical Committee. Though Debian users can take part in mailing-list discussions, only developers can vote in a general resolution or sit on the TC. Debian Developers (DDs) elect the Debian project leader every year. The DPL in turn appoints or reappoints the chairman of the Technical Committee and the secretary; these three roles must be distinct. The DPL also appoints delegates, such as the FTP master, who controls uploads of packages; release managers, who are in charge of supervising the release process; security team managers, who coordinate security issues with other projects; and Debian account managers or DAMs, a very sensitive position as they maintain Debian accounts and oversee the recruitment of new members, and can also expel or suspend developers. Often delegates are reappointed in their roles for many years.
The TC is a kind of supreme court which is supposed to arbitrate matters of technical policy, decide where developers’ jurisdictions overlap, and, when necessary, overrule developers. The secretary administers, and reports on, the voting process. Secretaries can stand in for the leader (as can the TC chairman) and they adjudicate disputes about interpretations of the constitution. The ultimate authority is the democratic will of all the developers, who can recall leaders, reverse decisions by leaders or delegates, or amend the constitution through a general resolution. In practice however, this is seldom used: in the ten years following the adoption of the Constitution in 1998, there have only been twelve general resolutions.
As for DPLs, their authority is qualified. The constitution states that, just like a traditional tribal chief, ‘the Project Leader should attempt to make decisions which are consistent with the consensus of the opinions of the Developers’. (14) Leaders make decisions for which no one else has responsibility, but should ‘avoid overemphasising their own point of view when making decisions in their capacity as leader’. (15) How can project leaders enforce their decisions? Their compliance arsenal is limited, as demonstrated when the DPL, in an effort to compel a recalcitrant developer to report on what he was up to, published an open letter to the developer in an attempt to shame him into action. (16) Because of the delays in processing new applicants, the status of Debian maintainer, situated between developers and users, was created in 2007. This authority level would be for users who had been maintaining a package for some time; they would be allowed to upload without going through maintainers. However, they would not have voting rights, nor would they have access to the debian-private mailing list or the Debian infrastructure. (17)
As has frequently been noted, external enemies serve to coalesce boundaries of exclusion and inclusion. The originating enemies of all free-software project, which motivate and sustain their existence, are entities which restrict hacker autonomy. Lehmann writes that such enemies include ‘anything and anyone which is perceived as prohibiting access, including copyrights, patents, and secret source codes, but also mechanisms that encourage dependence’. (18) Richard Stallman once declared that persecuting the unauthorised redistribution of knowledge by robot guards, harsh punishments, legal responsibility of ISPs and propaganda is ‘reminiscent of Soviet totalitarianism, when the unauthorised copying and redistribution of samizdat was prohibited’. (19) This kind of outburst is rare. Hackers in general, and Debian developers in particular, do not as a rule disparage proprietary software; its inferiority is taken for granted, not dwelt upon. This is because, as in the blogosphere, conflicts with the ‘same’ far outweigh in intensity those against the ‘other’.
A prime candidate for the role is a rival software distribution named Ubuntu. Financed by Mark Shuttleworth, a dot-boom entrepreneur, and his firm Canonical, Ubuntu’s strongpoint is the clockwork regularity of its releases: every six months, Ubuntu developers ‘freeze’ Debian, make a selection amongst the myriad Debian packages, and release them as an integrated system. Ubuntu’s ease of installation and its successful generation of a community network of support and development, complete with mailing lists, have proved popular. Debian’s original founder, Ian Murdock, who left the project, commented that Debian had ‘brought this fork on itself with its glacial pace’. (20) The Ubuntu website states (emphasis added) that ‘the Ubuntu project attempts to work with Debian to address the issues that keep many users from using Debian.’ (21) A developer justified leaving Debian for Ubuntu because he was tired of the frequent flame wars and because ‘having one person who can make arbitrary decisions and whose word is effectively law probably helps in many cases’. (22)
Conversely, some Debian users affirmed their distinction as true free-software aficionados: ‘most people who use Ubuntu (Not to insult them) are teenagers who want to use Linux in the same way “hip” people use Macs’. (23) Sometimes the hostility moved offline, for example at the annual Debian development conference debconf6 where someone ‘was attacked for wearing an Ubuntu T-shirt … while someone else was applauded for wearing a “Fuck Ubuntu” t-shirt’. (24) In contrast to Debian, Ubuntu’s updates had a clockwork regularity; and it was disturbing for volunteers to see others being paid for what they themselves were doing for nothing. (25) The rise of Ubuntu also risked turning Debian into a supermarket of components with little work being done on the crucial elements that work across packages. (26) But the biggest problem was the perception that as Ubuntu grew, it was effectively leeching off Debian, but not paying Debian back in the coin of the realm: improvements to the software. The Ubuntu website declares that bugs listed on the Debian Bug Tracking System (BTS) and fixed in Ubuntu are automatically communicated back to the BTS. Yet in 2008 a former Debian project leader declared that developers were unhappy about the relationship with Canonical, who they believed was not actively contributing back to Debian: ‘They’re not giving back as much as they claim to do.’ (27) In breaking the development code, Ubuntu was not behaving honourably.
What is the role of honour in Debian? Nicolas Auray argues that the ethic of the Debian project is a form of ‘moral heroism’ or ‘civic totalitarianism’ required by the participants’ constant mobilisation via the mailing lists. This generated a specific Debian ‘netiquette’. Members of the tribe have to demonstrate perfect self-control, temper their emotions and follow norms of humility. (28) That inventors require norms of humility to moderate an intense focus on originality and priority had been posited by Robert Merton in his sociology of the scientific field. (29) In Debian, humility serves to temper not priority, but authority over packages. Yet it is debatable whether humility really influences behaviour in an environment predicated on technical excellence, and which clearly constitutes a continuation of the confrontations of Usenet, as evidenced by countless references to ‘flame wars’ and ‘killfiles’ (and their distinctive *plonk* noise). In this context the threat of dishonour allows the lack of observance of the humility norm. Honour is less a bug in system than a fallback mechanism, an (archaic) justification for autonomous conflictuality. When a French user dared to criticise the lack of responsiveness of developers to user needs, a developer replied: ‘What am I, your servant? We are volunteers who have better things to do than listen to the inept ramblings of a minority of users who know better than us what they want to do.’ And the next day another developer added, speaking to the same user: ‘Contrarily to you, we don’t just watch, we play’. (30) The developer’s honour is rooted in being active and autonomous."
References
(1) Nicolas Auray, ‘Le Sens du juste dans un noyau d’experts: Debian et le puritanisme civique’, in Bernard Conein, Francoise Massit-Folléa and Serge Proulx (eds), Internet, une utopie limitée: Nouvelles régulations, nouvelles solidarités, Laval, Quebec: Presses de l’Université Laval, 2005.
(2) Nicolas Auray, ‘The decision-making process within a huge project: discussions and deliberations in Debian’, Libre/Open Source Software: Which Business Model? Calibre Workshop, Paris, 4 March 2005.
(3) Krafft, The Debian System, p. 53.
(4) Josh Lerner and Jean Tirole, ‘Some simple economics of open source’, Journal of Industrial Economics, Vol. 50, No. 2 (2002), pp. 194–327.
(5) Audris Mockus, Roy Fielding and James Herbsleb, ‘A case study of open source software development: the Apache server’, in Proceedings of the Twenty-second International Conference on Software Engineering, Limerick, Ireland, ACM Press, 2000, pp. 263–72.
(6) Krafft, The Debian System, p. 54.
(7) Bernard Conein, ‘Communauté épistémique et réseaux cognitifs: coopération et cognition distribuée’, Revue d’Economie Politique, No. 113 (2004), pp. 141–59.
(8) Bernard Conein, ‘Relations de conseil et expertise collective: comment les experts choisissent-ils leurs destinataires dans les listes de discussion?’, Recherches Sociologiques Vol. 35, No. 3 (2004), pp. 61–74.
(9) Auray, ‘Le Sens du juste’.
(10) Siobhán O’Mahony and Fabrizio Ferraro, ‘The emergence of governance in an open source community’, Academy of Management Journal, Vol. 50, No. 5 (2007), pp. 1079–106.
(11) Siobhán O’Mahony and Fabrizio Ferraro, ‘Managing the boundary of an “open” project’, Workshop on the Network Construction of Markets, Santa Fe Institute, 2003.
(12) Ibid.
(13) Auray, ‘Le Modèle souverainiste’.
(14) ‘5.3. Project Leader: Procedure’, Debian Constitution [online].
(15) Ibid.
(16) SH, ‘Re: Making Debian work: a question of trust indeed’, debian-project, 21 November 2007 [online].
(17) ‘General Resolution: endorse the concept of Debian Maintainers’, Debian [online].
(18) Lehmann, ‘FLOSS developers as a social formation’.
(19) Richard Stallman, ‘Copyright and globalisation in the age of computer networks’, in Rishab Aiyer Ghosh (ed.), CODE: Collaborative Ownership and the Digital Economy, Cambridge, MA: MIT Press, 2005, pp. 317–35.
(20) Ian Murdock, ‘Ubuntu vs. Debian, reprise’, Ian Murdocks’ Weblog, 20 April 2005 [online].
(21) ‘Community: Debian and Ubuntu’, Ubuntu [online].
(22) Matthew Garrett, ‘I resigned from Debian today’, LiveJournal, 28 August 2006 [online].
(23) MP, ‘Re: “I do consider Ubuntu to be Debian”, Ian Murdock’, debian-user, 19 March 2007 [online].
(24) Scott James Remnant, ‘Having left Debian’, Netsplit, 2 September 2006 [online].
(25) Martin Krafft, ‘Ubuntu and Debian’, Madduck, 2006 [online].
(26) Joey Hess, ‘The supermarket thing’, 21 October 2007 [online].
(27) Sam Varghese, ‘A conversation with Martin Michlmayr’, IT Wire, 31 January 2008 [online].
(28) Auray, ‘Le Sens du juste’.
(29) Robert K. Merton, The Sociology of Science: Theoretical and Empirical Investigations, Chicago: University of Chicago Press, 1973.
(30) Various authors, ‘Re: Critique constructive de Debian’, debian-devel-french, 29 September 2007 [online].
Expertise and Autonomy
Author's Note - Mathieu O'Neil on Online Tribal Bureaucracy and Expertise:
To be accepted, decisions by leaders must be legitimated by a meaningful relationship between the leader's role and an organisational structure. Online tribal bureaucracies are hybrid forms characterised by the cooperative production of free content, the overlapping of authority orders (bureaucratic traits are mixed with collective and charismatic traits); the prevalence of conflict; and deliberative procedures. In terms of economic efficiency online tribal bureaucracies have both advantages and disadvantages when compared to corporate bureaus and communes: there is less risk of misuse of internal resources by insiders than in traditional bureaucracies (though the risk of outsider misuse is strong in open projects) but conversely there is no legal responsibility for the well-being of participants, for example.
Conflict is rife. Elite projects are characterised by quarrels over the control of development, while in mass projects the herding of autonomous content producers by administrators can generate humiliation. There is a clear distinction between mass projects based on the participation of amateurs and elite projects based on the participation of experts. In one case anonymity is accepted, in the other it is impossible. But is anonymity, which allows the denial of responsibility, viable?
This question leads to another one, having to with the role and power of technical or technocratic experts. The reality in mass collectivist projects is that only a small minority of participants has the necessary expertise to understand and operate the complex technical infrastructure. This necessarily calls into question the ability of others to meaningfully engage in the democratic direction of a project. These questions are not new. But traditionally, in mass societies, nothing could be done to challenge the power of technocrats and technicians to make decisions that affect everyone. It remains to be seen whether tribal bureaucracies will find a way forward.