Power To The Edge
Book and security-related concept.
Book: Power to the Edge. Command... Control... in the Information Age. David S. Alberts , Richard E. Hayes ,with a Foreword by John Stenbit. U.S. Department of Defense. Command and Control Research Program, 2003. 300+ pages, pdf
URL = http://www.dodccrp.org/files/Alberts_Power.pdf
Definition
From the Wikipedia [1]
Power to the Edge refers to the ability of an organization to dynamically synchronize its actions; achieve command and control (C2) agility; and increase the speed of command over a robust, networked grid. The term is most commonly used in relation to military organizations, but it can equally be used in a civilian context. (http://en.wikipedia.org/wiki/Power_to_the_Edge)
Discussion
Network-centric warfare:
"Power To The Edge's radical ideas had been under investigation by the Pentagon since at least 2001. In UIAW, the concept of peer-to-peer activity combined with more traditional hierarchical flow of data in the network had been introduced. Shortly thereafter, the Pentagon began investing in peer-to-peer research, telling software engineers at a November, 2001 peer-to-peer conference that there were advantages to be gained in the redundancy and robustness of a peer-to-peer network topology on the battlefield. Colonel Robert Wardell said "You have to empower the fringes if you are going to... be able to make decisions faster than the bad guy".
Network-centric warfare/operations is a cornerstone of the ongoing transformation effort at the Department of Defense initiated by former Secretary of Defense Donald Rumsfeld. It is also one of the five goals of the Office of Force Transformation, Office of the Secretary of Defense." (http://en.wikipedia.org/wiki/Network-centric_warfare)
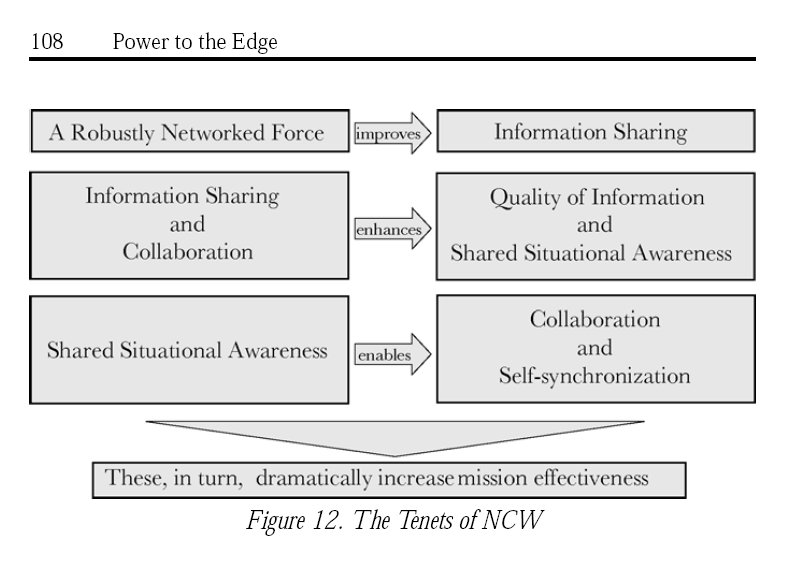
Principles
Power to the Edge advocates the following:
- Achieving situational awareness rather than creating a single operational picture
- Self-synchronizing operations instead of autonomous operations
- Information Pull rather than Broadcast Information Push
- Collaborative efforts rather than individual efforts
- Communities of Interest (COIs) rather than stovepipes
- "Task, post, process, use" rather than "task, process, exploit, disseminate"
- Handling information once rather than handling multiple data calls
- Sharing data rather than maintaining private data
- Persistent, continuous information assurance rather than perimeter, one-time security
- Bandwidth on demand rather than bandwidth limitations
- IP-based transport rather than circuit-based transport
- Net-Ready KPP rather than interoperability KPP
- Enterprise services rather than separate infrastructures
- COTS based, net-centric capabilities rather than customized, platform-centric IT
(http://en.wikipedia.org/wiki/Power_to_the_Edge)
Excerpted Graphs
Interoperability
page 138
Interoperability, the ability to work together, needs to simultaneously occur at a number of levels to enable entities to communicate, share information, and collaborate with one another.
The degree to which forces are interoperable directly affects their ability to conduct network-centric operations.
Interoperability must be present in each of the four domains: physical, information, cognitive, and social.
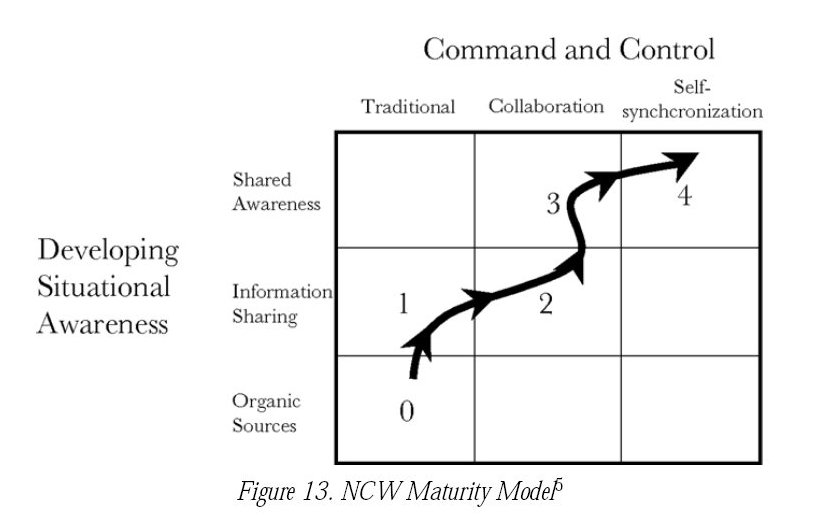
Developing Situational Awareness
page 139
LEVELS OF INTEROPERABILITY :
Interoperability can be understood as a spectrum of connectedness that ranges from unconnected, isolated entities to fully interactive, sharing enterprises.